Trying to migrate off Server 2012 R2 before the deadline? First time running a backup of your CA and suddenly you realize you can’t? Me too! The first error you probably see when you try to run a backup is as follows:
“Windows cannot back up one or more private keys because the CSP does not support key export. Do you want to continue and back up only the private keys that can be exported?”
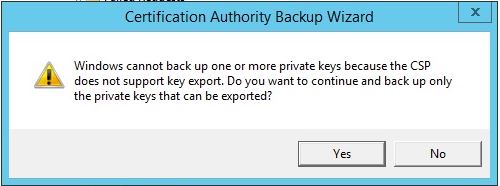
Clicking “Yes” sounds promising but then you get the next error:
“Keyset does not exist 0x80090016 (-2146893802 NTE_BAD_KEYSET)”
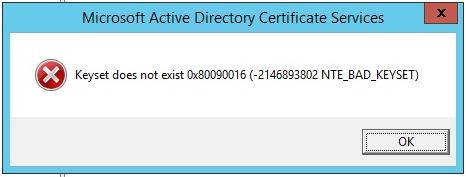
Clicking “OK” again just closes the window, and you quickly realize no backup happened.
Good news! after a call with Microsoft, this was pretty easy to fix.
- Open certsrv.msc
- Right-click the certificate authority
- Select properties.
If your CA looks like mine did, you’re probably going to see a few certificates listed on the General tab, many of which are either expired or revoked. These certificates are why the backup is failing.
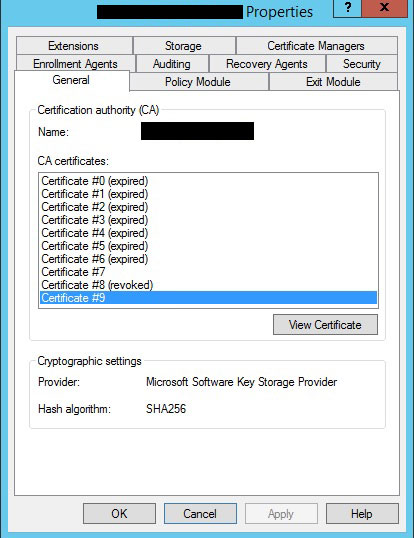
The certificates listed in this properties window are in the personal store on the CA. You can identify which certificate is which by comparing the thumbprints / expiration dates / etc. My first attempt to fix this was to archive the certificates what were expired. Unfortunately doing so resulted in a different error when making a backup, so don’t bother doing that:
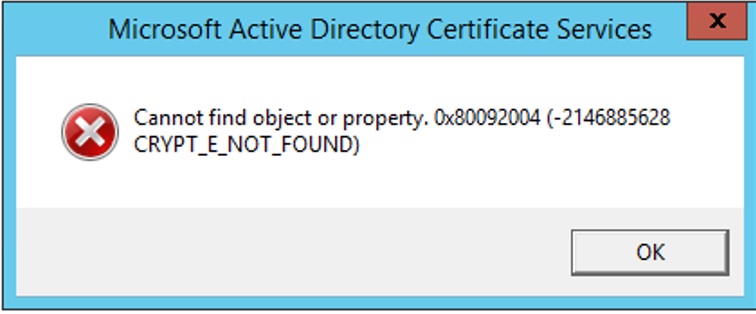
Cannot find object or property. 0x80092004 (-2146885628 CRYPT_E_NOT_FOUND)
The actual solution was to open the registry and navigate to HKLM\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\<name of CA>
Once here, locate the CACertHash REG_MULTI_SZ property. You’re going to see it has a list of different values. These values are the corresponding thumbprints of the certificates in the CA Properties window you had open earlier.
Before doing anything else, make a backup of the <name of your CA> key!
What you want to do is identify which values in this window correspond to the expired / revoked certificates, and replace them with a dash – leaving only the value(s) that refer to the valid certificate(s). Here’s what my view looked like after doing so (I’ve obviously blocked out the thumbprints that I left in place). You might notice that the order of the dashes and the two valid thumbprints align with the order of the certificates listed in the CA’s properties window. Obviously double check yours before just blindly assuming they are the same order, but odds are they are.
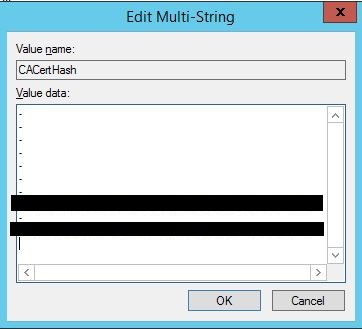
After clicking OK go ahead and reboot the server. Once it is back online, you should be good to go! Opening the properties window of the CA again should now only show the valid certificate(s) you left in the registry, and most importantly backups should now work!

Excellent and to the point problem target.
Works, cheers